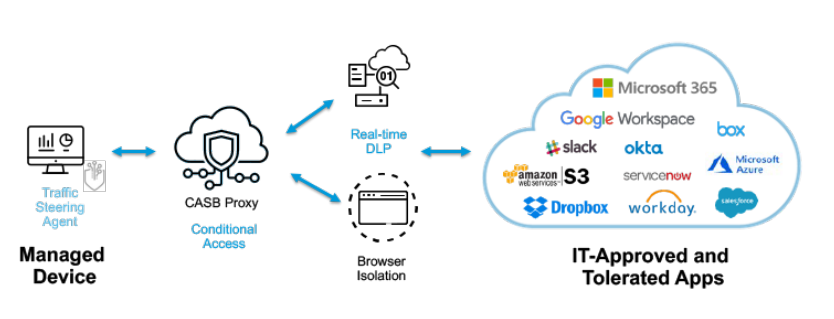
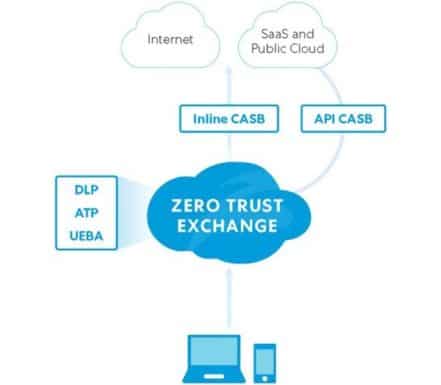
For firm personnel accessing cloud-based apps, Cloud Access Security Brokers (CASB) solutions provide an additional layer of protection.
In addition, the program acts as a bridge between staff members and cloud services and enforces security regulations. Through this, businesses can extend on-premise security controls beyond their local infrastructure or network.
In fact, cloud-based or on-premise software that acts as an intermediary between a cloud application user and a cloud service provider forms a typical CASB solution. From here, the solution enforces the company’s security standards to protect users, data and cloud apps.
Due to cost-effectiveness, ease of use, and support for a remote workforce, cloud-based apps are becoming more and more popular among enterprises. Unfortunately, there are a number of security risks associated with using cloud apps. Cloud-based apps typically require additional protection, such as that provided by a cloud access security broker solution because traditional perimeter security that protects on-premises is typically insufficient.
When individuals and devices access cloud apps and data, CASB solutions are primarily used to identify security threats and regulatory violations. In addition to mitigating security risks, CASB will monitor software systems for any unusual processes or behavior. In an ideal world, tools would react and notify administrators when they see an anomaly.
How CASB Solutions Help Businesses Enhance Security
CASB tools give businesses the ability to;
- Boost the security of cloud apps and authorized users. It also assists in locating illicit access, questionable activity, and unapproved cloud services.
- Keep an eye on and control user behavior, managed and unmanaged devices, and the use of authorized cloud-based apps.
- Obtain insight into the security posture and compliance concerns of the company.
- Improve the cloud services’ capacity for threat detection and response.
- Safeguard data, cloud apps, and consumers of cloud services.
Qualities That Make a Successful CASB Tool
The four main pillars of a typical CASB tool are compliance, data security, risk prevention, and visibility. While there may be differences between CASBs in terms of installation, functionality and performance, a reasonable solution should ideally contain the following essential components.
- Give users and devices access to cloud-based apps and their activity.
- Enforce access restrictions, encryption, and local security regulations for cloud-based services.
- Provide an additional degree of protection for users, data, and cloud apps.
- Enable businesses to adhere to common principles around security, data loss prevention and other matters.
- Establish a secure channel of communication between end users or staff and the cloud service provider.
A wide array of tools with varying capabilities are available today to help you choose the ideal tool for your environment. Top Cloud Access Security Brokers (CASB) are listed below.
1) Cisco Cloudlock
The first on the list of Cloud Access Security Brokers (CASB) is, Cisco Cloudlock is an easy-to-use, automated cloud-native CASB that enables businesses to protect their people, data and cloud applications. Security teams can better understand and protect their environment with broader visibility into cloud applications and shadow IT that offers a complete solution.
Features
- Automates policy-based cloud app control, including removing apps that exceed permission limits and have high-risk ratings.
- Employs cognitive technologies such as machine learning and user analytics to identify and prevent unusual activity, hostile insider threats, hacked accounts, unwanted access, inadvertent exposure, and policy violations.
- By providing automated, policy-based shadow IT enforcement solutions that can be used to restrict problematic activities and apps based on permissions and risk levels, you can lessen the risk associated with shadow IT.
- Uses configurable policies to identify and prevent data loss or theft. Thanks to this, teams can now properly secure sensitive data both in transit and at rest.
- Teams can easily secure access and protect cloud apps, users and data with this complete API-based CASB solution that’s easy to set up and run.
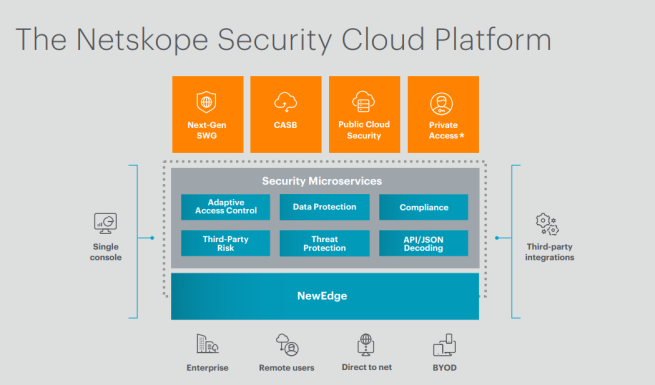
2) Netskope Security Cloud Platform
For customers using cloud-based apps, the NetScope Protection Cloud Platform offers complete protection and enhanced visibility independent of device or location. The platform protects against various threats, malware, and data breaches for both users and apps. Major cloud services like Microsoft Office 365, AWS, Google G Suite, Box, etc., are supported by the tools.
Features
- Establish better security policies and gain better visibility to help you detect and prevent data loss risks from both internal users and outside criminals.
- Makes it possible for security personnel to quickly find and monitor both managed and unmanaged cloud apps for their company. With the help of this technology, enterprises can guarantee compliance and keep an eye on security threats around them.
- Prevent unauthorized persons, such as cybercriminals, aides, hostile insiders, etc., from accessing or downloading sensitive data. It also helps prevent data leaks, allowing you to differentiate between personal and business accounts. Additionally, it monitors the cloud-based platform in real-time and prevents illegal data access, uploads, and downloads before they happen.
- Find and fix setup errors in your security systems and cloud-based apps.
- Maintain a strong security posture for your SaaS platform.
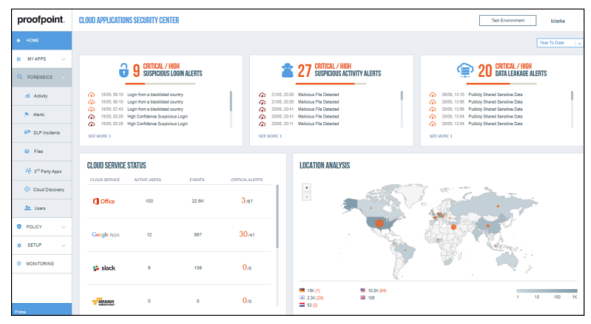
3) Proofpoint
A cloud-based CASB solution called Proofprint helps businesses securely access, control and manage their cloud data and apps. Advanced threat detection and protection features are included with the Cloud Access Security Broker solution. Due to its agentless architecture, enterprises can quickly and easily implement security solutions.
Features
- Provides insight into how cloud services are used globally by applications and users.
- Advanced DLP options, including templates, smart identifiers, rules, dictionaries, and more, are integrated. It also includes accurate and effective DLP policies that accelerate the deployment, identification, and response to threats that compromise cloud data.
- Prevents risks of data oversharing, non-compliance, malicious files and account breach
- Monitoring user behavior for strange behavior, suspicious login attempts, and potential data breaches. The program offers automated account compromise detection and unusual activity response.
- Enables teams to implement uniform data loss prevention measures for both cloud and on-premises applications and services.
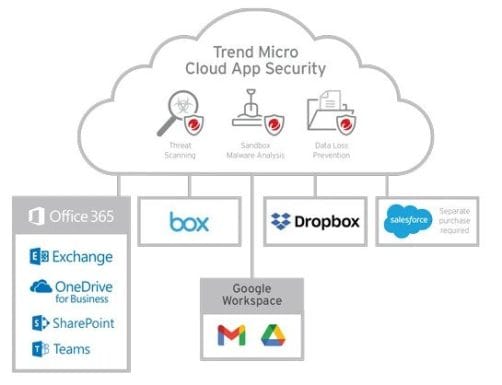
4) Trend Micro
One of the best ways to protect systems and data from various threats, including sophisticated attacks, is to use Trend Micro Cloud App Security. Additionally, it protects cloud-based programs, including cloud file sharing, G Suite, MS Office 365, email, and collaboration.
Features
- Enforcing compliance regulations on a variety of cloud-based file-sharing platforms, such as Box, Dropbox, OneDrive, Google Drive, and other online systems.
- State-of-the-art security measures to protect against ransomware, malware, email compromise, and other threats on a variety of Internet systems.
- Sandboxing uses advanced technologies, including analytics, machine learning, and others, to detect, identify, and respond to a variety of threats.
- Trend Micro helps businesses establish and enforce data loss prevention policies and compliance with cloud file-sharing services, in addition to providing protection against attacks. Before transferring information to the cloud, it also checks all files, including files on devices and remote employees.
- Apex One easily integrates with other Trend Micro security products, including Endpoint Protection.
5) Zscaler
One of the leading CASB solutions that is easy to set up and use is Zscaler, which guarantees secure access to cloud apps independent of a user’s device, network, or location. The system offers centralized policy and governance enforcement with advanced cloud application security and configuration management.
Features
- Security system complexity and costs are reduced by a unified, automated, and scalable web-based solution because it does not require the deployment of many different components.
- Ability to analyze large volumes of encrypted network traffic, protecting systems from various threats and possible data loss or theft.
- It protects data when it is at rest and in transit. In addition to giving cloud-based apps an extra layer of security, it also gives users more control and comprehensive access to their data and behavior.
- Uses advanced data classification technologies to accurately identify specific data, forms, and values that need to be protected. Additionally, it can recognize characters in image files using optical character recognition.
- Reducing the potential attack area and guaranteeing secure access to cloud apps. This tool monitors and handles a variety of security concerns, misconfigurations, and compliance issues.
- To maintain security, identify and protect data while in motion and at rest.
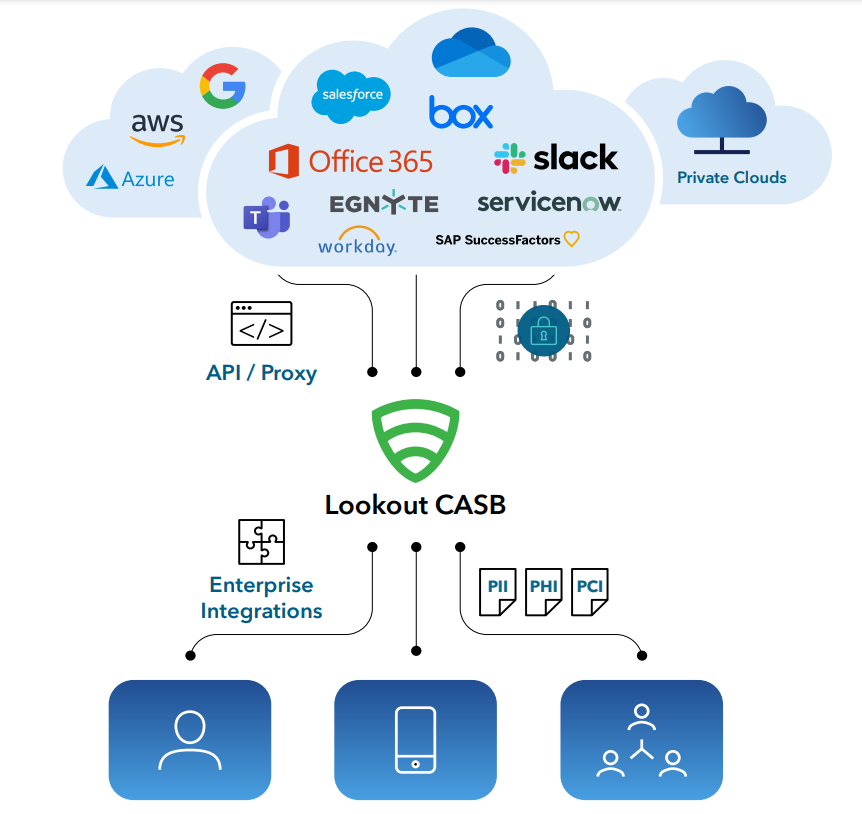
6) Lookout
A robust, feature-rich CASB solution that helps businesses protect their cloud apps and users is called Lookout Cloud Access Security Broker (formerly Cipherworld). It provides complete security, compliance enforcement, and end-to-end data protection in the cloud. The technology gives administrators greater visibility into their cloud apps through an intuitive interface.
Features
- Ensures that data is permanently encrypted and only authorized access is allowed.
- Monitor user behavior so security professionals can observe the apps being used and ensure compliance.
- Advanced key management with expiration, rotation, and other security-enhancing features
- With built-in capabilities that help businesses automatically enforce regulations that ensure data leaks, potential threats and other vulnerabilities are detected, data loss prevention (DLP) enhancements
- Proactively monitors threats by monitoring users, data and devices and generating useful reports.
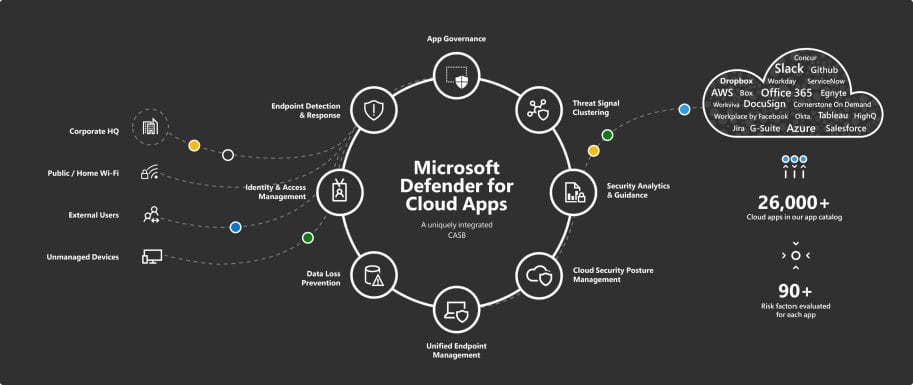
7) Microsoft Defender for Cloud Apps
Microsoft Defender for Cloud Apps combines several security measures with the flexibility to accommodate different deployment options. CASB systems also include other capabilities, such as log collection, reverse proxies, and API connections.
With its advanced analytics features, Microsoft CASB can detect and counter a variety of cyber attacks on platforms operated by Microsoft as well as independent cloud service providers. It also offers extensive visibility and control, protecting data both in transit and at rest.
Features
- Centralized management and ease of installation characterize this solution, which integrates with popular Microsoft services and deployments. Additionally, it offers a number of automated features that eliminate manual labor, accompanying errors, and inefficiencies.
- Prevent unauthorized or vulnerable devices or people from accessing or downloading sensitive data.
- Implementing real-time session controls will enable secure communication between the organization and outside parties.
- Using its audit trail feature, administrators can monitor device and user activity for forensic analysis.
- By recognizing and blocking strange activity, rogue apps, ransomware, high-risk exploits, and other threats, you can protect cloud apps, users, and data.
- Review and implement measures to ensure your cloud-based services and apps comply with applicable regulations.
8) Palo Alto
The last in the list of Cloud Access Security Brokers (CASB) is Palo Alto. A good option that offers several advanced security features is Palo Alto Networks’ CASB. It covers things like improved threat defense, threat identification, data governance, and user behavior tracking. Moreover, it easily integrates with other Alto security products, such as firewalls, access control, and others, to offer complete cloud app and data protection.
Features
- Advanced data loss prevention (DLP) capability uses deep learning, OCR, national language processing, and other intelligent technologies.
- Features enhanced visibility and threat discovery to identify and control threats.
- Use machine learning technology, context-aware policies, and enhanced data protection to protect data and prevent leaks.
- Monitor user behavior to identify, prevent, and notify when any unusual activity occurs, including repeatedly failing to log in, logging in unexpectedly or from different locations, Abnormally high usage, etc.
- Enforce compliance and data governance standards by identifying and resolving any regulatory violations, including PCI, PHI, GDPR, and other laws.
That’s it for the list of Cloud Access Security Brokers (CASB) Solutions.
ALSO SEE:
- Amazon Price Trackers
- Windows VPS Hosting
- Forex VPS Hosting
- Minecraft Server Hosting
- VPS Hosting Solutions
- Cloud Hosting Websites
- Conversion Tracking Software
Abstract
CASB solutions extend local infrastructure and an organization’s on-premise security systems and policies to cloud services. Between users and cloud services or apps, security software or platforms typically act as a barrier, monitoring user activities and preventing unwanted or unusual activities such as downloads, viruses and other online threats. Stop the
Additionally, CASB solutions support the implementation of multiple security regulations, guaranteeing complete security of cloud applications, users and data.